The cybersecurity domain provides a breadth of opportunity for tech professionals. From analyzing malware to managing a division of cyber defenders, a career in cyber keeps you on your feet for decades!
Companies’ reliance on technology has accelerated tremendously due to the pandemic. Important data floats in a cloud anyone can access in seconds from anywhere. Connectivity amongst dispersed teams has never been better. But, connection comes at a cost.
Hackers near and far have taken advantage of digital connectivity to attempt dangerous cyber attacks and ransomware. Hackers stealing data, infiltrating networks, and compromising systems cause billions of dollars in damages on a yearly basis.
Can the world stop hackers? That’s where the cybersecurity sector comes in to save the day! A multitude of positions, each with special skill sets and responsibilities form the cybersecurity sector.
Every cybersecurity professional, from the entry-level Cyber Analyst to the Chief Information Security Officer (CISO), contributes to the fight and defense against hackers across the globe.
Careers in cybersecurity provide an exciting journey and rewarding compensation for life. There are always more hackers to tackle and more challenges to meet.
Cyber Analysts and Team Leaders
A fresh graduate from an IT program will typically start as a Security Operations Center (SOC) Analyst. This job role involves working in conjunction with other SOC Analysts to identify and neutralize cybersecurity incidents.
Additionally, SOC Analysts conduct threat and vulnerability analyses to find areas of improvement within an organization’s IT infrastructure. Constantly finding and eliminating weak points decreases the chances of hackers penetrating companies’ IT infrastructure.
Cyber and SOC Analysts professionals must have strong attention-to-detail and remain calm under pressure. This position is also dynamic, as the problems a Cyber Analyst faces on a day-to-day basis change.
A cyber team is usually run by a team leader. The leader usually has the most cyber experience and reports to management. Leading a team requires management skills, a strong sense of collaboration, and the ability to work with people of various backgrounds.
Cybersecurity Specializations
SOC Analysts can build a diverse experience in their position for many years! However, some find that taking on more cyber concentrations is helpful in getting a wider perspective and progressing to management levels.
One such specialization in cybersecurity is the Cyber Forensics Investigator. With large-scale crime operations, investigators are the cyber professionals who have the skill set to uncover, analyze, and prevent this type of attack from reoccurring.
As Cyber Forensic Investigators gain experience, they can level up, handling complex intelligence and malware analysis.
A Cyber Forensics Investigator handles crime after the fact. Cyber Hunters, on the other hand, specialize in preventative cyber analysis, stopping attacks before they even happen. Cyber Hunters think from the perspective of a hacker to determine where the weaknesses can be found.
Malware analysis is another specialization. This sector Involves deep diving into discovered viruses, trojans, and ransomware. Each type of malware has unique characteristics that can be dissected. Learning how a malware attacks allows the cyber team to formulate a plan that combats the malware, strengthening the overall IT infrastructure.
Another subset of cyber roles includes Penetration Testers, Social Engineers, and Industrial Control Systems Specialists.
Penetration testing is a measure implemented by Cybersecurity Specialists to test a company’s computer system. By simulating a full-scale attack, companies can discover if there’s a vulnerability with the software, APIs, frontend, or backend servers. The testing shows where and how hackers can penetrate and cause harm, and allows the development team to improve application security.
Social engineering is a unique computer attack. Rather than a virus or malware, people can coerce other people to get into a specific computer system. The most popular form of social engineering against companies is phishing.
Phishing involves hackers sending emails, texts, or phone calls appearing as a trusted source, such as a bank, government office, or even senior management, and asking for confidential information, such as social security numbers, passwords, or wiring information.
Certain cyber professionals are trained in social engineering techniques and can implement preventative measures to combat this unique type of threat.
Lastly, cyber professionals may concentrate their efforts in preventing cyber attacks on industrial control systems. Industrial control systems are large scale processes that include manufacturing and product creation.
Making items on a large scale has never been easier due to automation and AI. Industrial Control Systems Specialists ensure production and automotive systems in factories run efficiently and securely, without interruptions by hackers and hostile states.
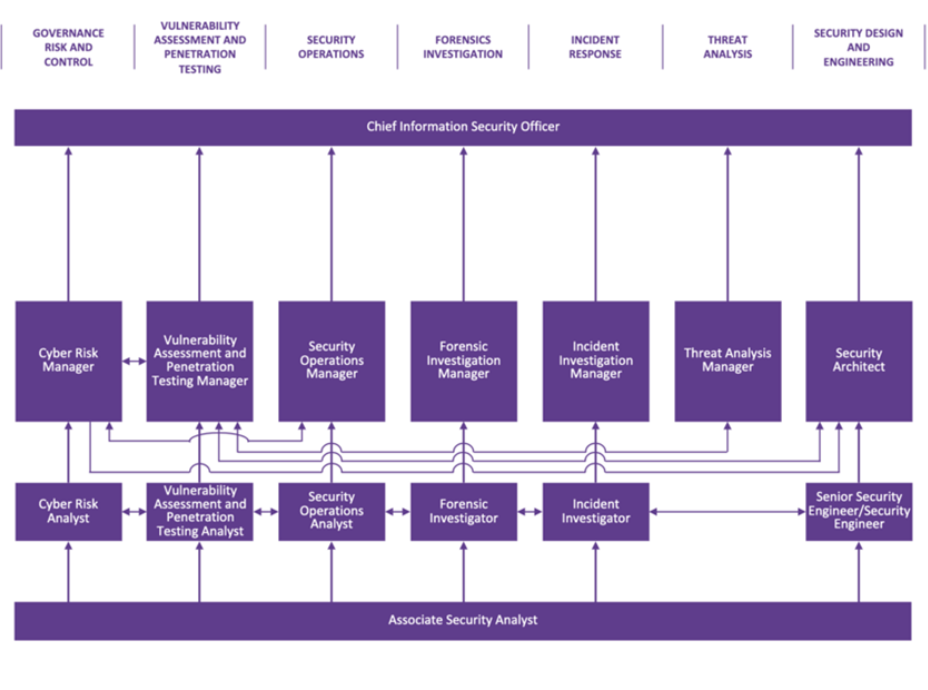
Senior Cyber Roles
With years of experience combating malware attacks, many Cybersecurity Specialists go on to take executive cyber roles.
Roles as manager, director, or Vice President of Information Security or Cybersecurity, lead teams and operations, take responsibility for complex challenges, and report to the Chief Information Officers (CIO) or Chief Information Security Officers (CISO).
The two top common leadership roles cyber professionals aspire to attain are the Chief Information Officer (CIO) and the Chief Information Security Officer (CISO). The positions do have overlap, but both have somewhat different functions.
The CIO works to create effective strategies and initiatives within a company to improve IT infrastructure and data management. The CISO, who sometimes reports to the CIO, handles the security, protection, and maintenance of information, data, and other digital assets. Both the CIO and CISO have peak cybersecurity skills and a strong business acumen.
The Time is Now
The tech sector used to require academic degrees to enter the cybersecurity field. However, rapid digitization has resulted in cybersecurity demonstrating one of the largest labor shortages in the world.
What does this mean? Now is the perfect time to get your foot in the cybersecurity door. When a student graduates from an entry-level cybersecurity program, not only do they have a set of baseline skills, but they now can elevate their position through cyber specialties.
Wawiwa Tech offers two entry-level Cybersecurity Specialist programs for people with or without an IT background. Shorter upskilling courses in all the aforementioned specialties are also available – Cyber Forensics Investigator, Cyber Threat Intelligence Hunter, Malware Analyze, Penetration Tester, and Industry Control Systems Specialist.
As more cyber analysts enter the field and eventually get promoted to CISOs, we are heading towards a brighter future and a safer internet for all!



